While most sites and applications in the digital era have begun moving towards deploying two-factor authentication (2FA) of users, a lot of them still depend on SMS based 2FA. Until recently, one such website was Twitter- one of the largest social networks. Twitter updated their Two-Factor Authentication (2FA) process, allowing users to go for 2FA without the need of a phone number.
The update happened particularly after Twitter CEO Jack Dorsey’s own personal account was compromised when a hacker got access to SMS-based two-factor authentication meant for Dorsy. Twitter also announced in a separate instance that phone numbers used for 2FA on its service had been used personalised advertising, all by accident.
Why You Need To Be Cautious Against SIM Based 2FA
Passwords alone are vulnerable against cyber attacks, especially on the off chance that you reuse passwords across multiple accounts. Numerous individuals reuse passwords at different sites and, when one site’s password database gets attacked, user passwords can be utilized to sign in to other accounts also. This is where 2FA comes in. But, if you are using SMS based authentication, you are still not entirely safe.
An attacker could impersonate you and move your SIM to another telephone using SIM porting or SIM swapping. In SIM swapping attacks, attackers persuade the telecom to switch the target’s SIM card with their own. This enables them to get access to victim’s texts, thus getting past SMS-based 2FA. This is precisely what happened when Jack Dorsey’s account was hacked.
The phone number associated with the account was compromised due to a security oversight by the mobile provider. This allowed an unauthorized person to compose and send tweets via text message from the phone number. That issue is now resolved.— Twitter Comms (@TwitterComms) August 31, 2019
According to experts, individuals who are probably going to be especially targeted by attackers ought to stay away from SMS-based confirmation. For instance, in case you’re a government official, journalist, a celebrity or businessman, admin with access to enterprise networks, you could be at the target of an SMS-based attack. SMS messages can also be intercepted through a basic flaw in the SS7 protocol used to transmit the messages.
What Are The Other 2FA Options Which Are More Secure Than SMS?
Apart from SMS-based authentication, there are additionally different kinds of two-factor authentication techniques, including applications that produce temporary security codes and physical security keys you need to plug into your PC.
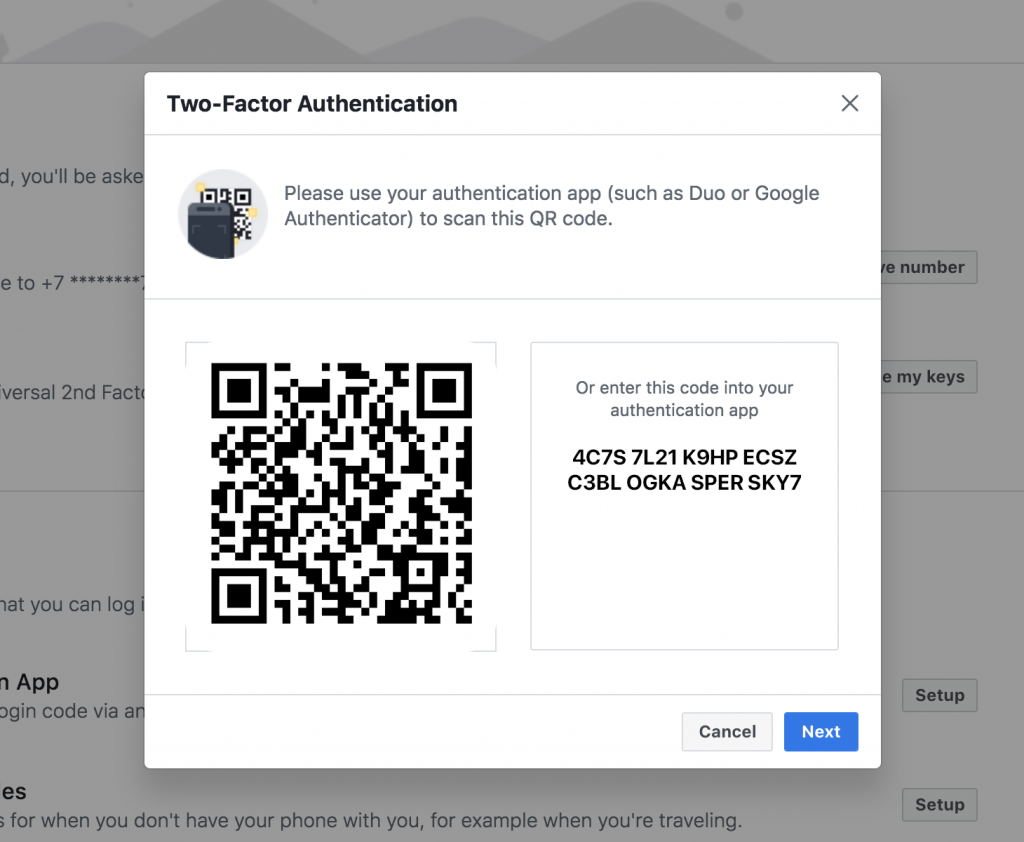
Let’s first talk about app-based 2FA like Google Authenticator which can be downloaded and installed on Android and Apple mobile devices. To use the service, go to the security settings of the web service that you want to use the app with, select 2FA option (if the service lets) and you will be shown a QR code that can be scanned directly into the 2FA app. Now, one thing to remember here is that contrary to popular belief, app-based 2FA can be easily backed up if you write down the private key shown at the time of scanning the QR code. So, please do that in case your device is lost.
Now, once you scan the code with the app (Google Authenticator), it will start generating a new one-time code every 30 seconds. The codes are generated using the key (known only to you and the server) for a particular time each 30 seconds synchronously. When the web service checks that the code is the same for you and the service, it authenticates you. This algorithm used to generate app-based 2FA codes is called OATH TOTP (Time-based One-Time Password) which is the standard technology used for app-based 2FA.

Apart from app-generated tokens, there is also the option of hardware tokens based on the U2F (Universal 2nd Factor) standard, created by the FIDO Alliance. U2F hardware tokens work when you connect the U2F token (saved inside a hardware device) and register it on a web service (if it is compatible). When registering a token on a service, a pair of cryptographic keys is created — private and public. The public key is saved on the server, and the private one is stored in a Secure Element chip, which never leaves the device. And every time, you will need to log in, you may need the physical device to plug in with the service. You can also register multiple such devices and even back up the private key in case you lose one device.
The most prominent example of U2F is YubiKey, made by Yubico- which has been one of the pioneers of U2F standard and an important member of FIDO alliance. But U2F-compatible devices are sold by different because U2F is an open standard, not proprietary. Google also recently launched U2F authenticators under the brand name Google Titan Security Keys.