From ID cards to diagnosis, the availability of personal data has never been this high. Google, in a move to fortify its stance towards data privacy, open sources a new tool Private Join and Compute.
With Private Join and Compute, Google goes old school with cryptography by combining two fundamental cryptographic techniques to protect individual data:
- Private set intersection allows two parties to privately join their sets and discover the identifiers they have in common.
- Homomorphic encryption allows certain types of computation to be performed directly on encrypted data without having to decrypt it first, which preserves the privacy of raw data. Throughout the process, individual identifiers and values remain concealed. of values associated with marked encrypted identifiers – without learning anything about individuals.
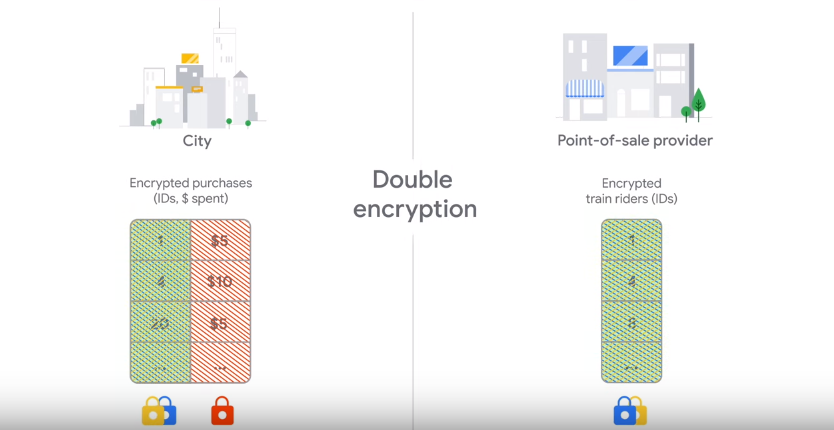
Secure Sharing with Private Join And Compute
For example, if Bengaluru’s head of city planning wants to draw insights from the ride data in comparison with the data from sales on local businesses, the data is shared from the transport services like metro and also from local stores.
This kind of data usually contains millions of rows, considering a densely populated city like Bengaluru, it wouldn’t be surprising. So, it is very important to ensure no leakages during the sharing of this data between the providers.
Private Join and Compute is a cryptographic protocol that helps users to share and run aggregate computations on sensitive data without running into the danger of revealing private data about individuals.
Each party can apply private encryption that keeps its data unreadable to others. Both the parties share this data encrypted with one layer and then each of these parties applies another layer of encryption and shuffle the order. At no point in this process, either party or third party can sneak in to access datasets outside of their own.
This combination of techniques ensures that nothing but the size of the joined set and the statistics (e.g. sum) of its associated values are revealed.
In the above example, the only results that can be inferred are people who have used a certain transport and have also purchased at the store; the overlap and not the personal data.
However, the team behind this work suggest the users to recommend performing a careful risk analysis before using Private Join and Compute If the underlying data is sensitive. This is to ensure that neither party has an incentive to deviate from the protocol.
Here are a few use cases highlighted by the developers at Google security:
- Public policy – if a government implements new wellness initiatives in public schools (e.g. better lunch options and physical education curriculums), what are the long-term health outcomes for impacted students?
- Diversity and inclusion – when industries create new programs to close gender and racial pay gaps, how does this impact compensation across companies by demographic?
- Healthcare – when a new preventative drug is prescribed to patients across the country, does it reduce the incidence of disease?
- Car safety standards – when auto manufacturers add more advanced safety features to vehicles, does it coincide with a decrease in reported car accidents?
Joining Hands For Privacy
Google’s open-source availability of Private Join and Compute, a new type of secure multi-party computation (MPC) that augments the core PSI protocol to help organizations work together with confidential data sets while raising the bar for privacy. The success of this also will embolden Google’s effort to apply this protocol for applications in collaborative machine learning, user security, and aggregated ads measurement.
Open source tools like Private Join and Compute have the potential to accelerate the next generation of security and privacy breakthroughs, which has been lacking from the current state-of-the-art toolkits for data processing.
Know more about the tool here