|
Listen to this story
|
In 2016, The DAO, first-ever decentralised autonomous organisation (DAO) built on Solidity, lost 3.6 million Ether, worth about $70 million (about $1.4 billion in today’s price), to the re-entrancy attack.
The hacker first made a small contribution to The DAO and then requested many withdrawals. The smart contract failed to update itself after the withdrawal and the attacker continuously called the withdraw function to drain the contract’s funds.
In this kind of attack, the attacker re-enters the function over and over again while calling it; thus the word ‘re-entrancy’.
The re-entrancy attack on The DAO exposed the vulnerability in the EVM-based smart contract that also led Ethereum to hard-fork and create a completely new blockchain called Ethereum 2.0.
After the attack, developers were educated to use the “Checks-Effects-interactions” pattern and “Reentrancy Guard” to prevent similar attacks.
However, six years later, contract vulnerability attacks (like re-entrancy) are still happening and the vulnerability is still causing the loss of millions of dollars every year.
DeFi is the prime target
DeFi Pulse estimates that DeFi has a total value locked (TVL) of more than $56 billion. The sum is substantial, but it represents a significant decline from TVL in DeFi, which exceeded $110 billion in 2021. The recent stablecoin crash is primarily to blame for the decline of TVL. However, losses resulting from the DeFi token and DeFi protocol vulnerabilities can also help explain some of the decline in TVL.
According to the REKT Database of cyber-attacks, DeFi protocols have lost $4.75 billion in total due to scams, hacks, and exploits. Out of $4.75 billion lost, only $1 billion was returned.
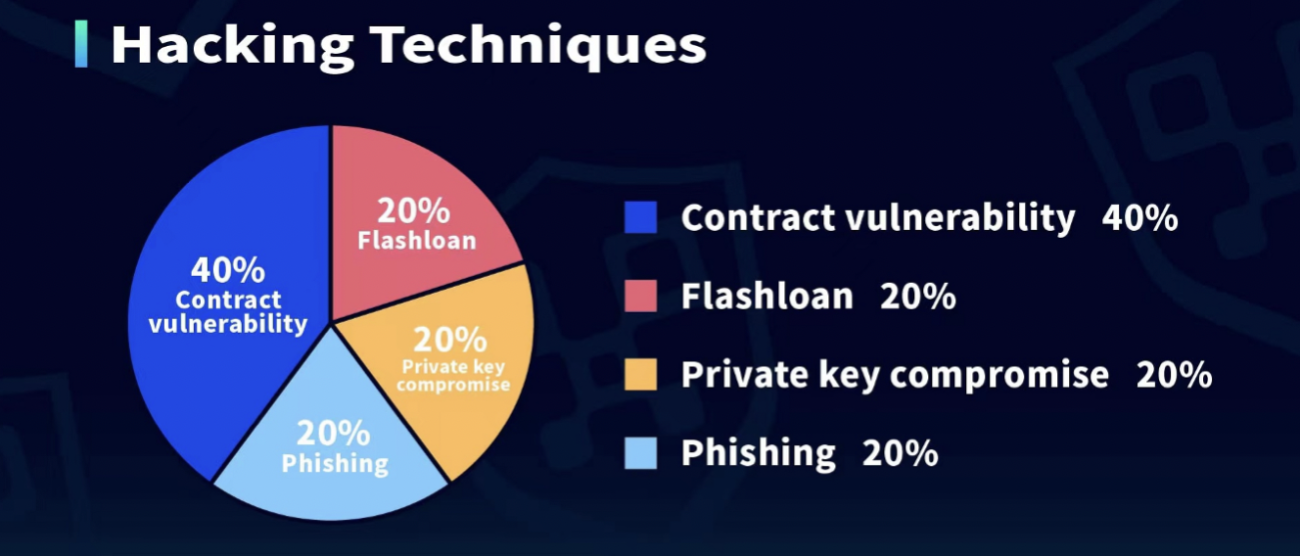
This year alone, Web3 security incidents have swindled about $2.3 billion from various Web3 platforms, according to Web3 security platform Beosin. The majority of the attacks have happened on DeFi platforms. Of these attacks, a significant portion were related to contract vulnerability, re-entrancy attacks specifically, followed up by flash loan, phishing and private key compromise.
(Credit: Beosin)
Fei Protocol, Paralumi, Grim Finance, SIREN protocol, CREAM Finance and others are some of the DeFi platforms that suffered contract vulnerability attacks in the last one year.
In April 2022, the Fei protocol was the victim of an $80 million hack. In December 2021, Grim Finance’s safe function was exploited for about $30 million loss in tokens.
Flash loan attack is another most common attack on DeFi platforms. Flash loan is a smart contract that creates a loan in cryptocurrency where borrowers can borrow millions of dollars worth of tokens with absolutely no collateral. However, the borrower has to pay the flash loan back in the same transaction that they took with it—in about 13 seconds, a time-period required for an Ethereum blockchain to be validated. Recently, DeFi platform Beanstalk Farms became the victim of a flash-loan attack and lost about $182 million.
Flash-loan attack: Beanstalk’s case study
Like many other DeFi projects, Beanstalk’s developers incorporated a governance system that allowed contributors to vote jointly on coding modifications. They would then be granted voting privileges in proportion to the value of the tokens they owned—resulting in a vulnerability that would ultimately prove fatal to the enterprise.
During the security breach, the attackers exploited the vulnerability that “the number of votes in the voting contract is calculated from the proposal token holdings of the account”. They borrowed over $1 billion via flash loan in exchange for tokens, transferred them into the mining pool and obtained proposal tokens to pass the proposal without other votes. They successfully executed and passed the proposal—consequently withdrawing the project’s funds with a gain of approximately $80 million.
Decentralisation: You just can’t change the law
While DeFi projects claim to increase the efficiency of crypto transactions, a large portion of the software’s underlying code is public, thereby making it available for anyone online to search for potential security flaws that they might be able to exploit.
“Since ‘code is law,’ there is oftentimes no recourse for a decentralised platform in case of an exploit,” said Stephen Llyod Webber, Product Marketing Lead, OpenZeppelin, a Web3 platform that provides security products to dApps and audits for decentralised systems.
In conversation with Analytics India Magazine, Webber explained that while legacy services can have backups and options to “roll back” their databases, everything that happens on a truly decentralised blockchain is more or less irreversible. Furthermore, even if there is a way to “reset” some malicious activity, this usually means that a platform is essentially centralised to some extent.
How to secure the law (code)
Web3 platforms need to address these security issues to witness global mass adoption. While no digital system can be “fully secured,” there are ways to mitigate these risks as much as possible. For example, rigorous security reviews and real-time monitoring frameworks can greatly help Web3 platforms reduce their vulnerability—particularly, when this monitoring is integrated with the ability to automate incident response.
“OpenZeppelin offers a product called Defender that helps developers automate smart contract operations and deliver high-quality products with lower risk,” said Webber.
He added that the product ‘Defender’ allows developers to manage all their smart contracts, including access controls, upgrades, and pausing. Defender also works with popular multi-signature wallets such as ‘Gnosis Safe’.
Experts believe that every Web3 enterprise needs to take its security very seriously and use the best tools available to do so. While very few digital systems can be called truly impenetrable, a certain level of protection can be achieved when attacks become unviable or too expensive for perpetrators to conduct.
Bug bounties can be very effective for preventing malicious exploits because they offer a substantial reward for addressing any security issues found in a given protocol. Constant real-time monitoring can significantly help Web3 platforms to be well-positioned to respond to any existing or emerging exploits, or even automate the response to a given type of security incident—removing the need for human intervention entirely.

























