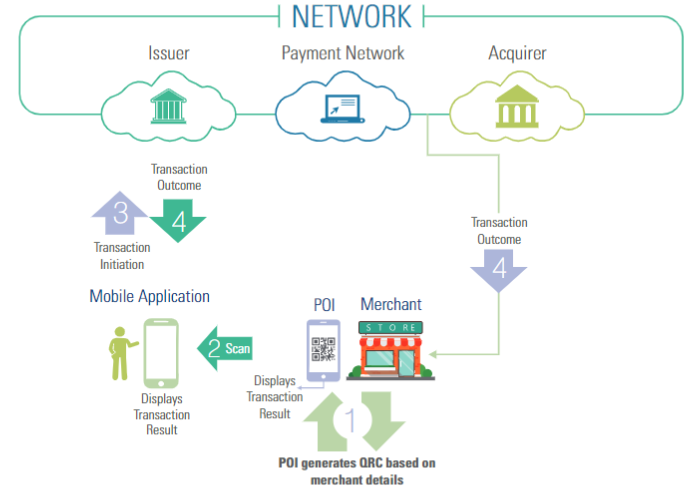
The turn of this millennium witnessed a heavy smartphone penetration in society. This also led to the development of electronic payments and digital wallets. Payment modes like scanning QR codes have taken the central stage. Today the majority of transactions that happen in retail shops or other bill payments are using this system.
QR codes were invented in 1994 by Denso Wave, a unit of Japan’s largest automotive parts maker, to allow for quick scanning when tracking vehicles during the assembly process. It was initially designed for an automobile factory, which later found applications in other industries.
Quick Response or QR codes are two-dimensional barcodes that visually encode bits of information represented as black square dots placed on a white square grid.
Currently, over 23% of Trojans and viruses are transmitted via QR codes. On the 25th anniversary of QR codes, its creator, Masahiro Hara wants to make QR scanning more secure.
Usually, in the case of QR scanning, possible scenarios of attacks can be summarised as follows:
- QR codes cannot be hacked. One way hackers to infiltrate this system by changing the QR code added in the poster. These fake posters can be circulated in the public domains and clueless customers scan these fake QR codes and end up visiting phishing websites.
- This usually happens because of the increase in the number of mobile users. Mobiles make it hard to verify the full link in the address bar. This makes users more vulnerable. When they use this phishing page to login, their passwords are compromised.
- An attacker might set up a fake website and redirect users by changing the QR Code. This is dangerous if some form of credentials are needed to access the website. The user has no possibility to verify that the link is not modified.
- SQL injection is another form of attack that occurs when SQL queries are made with user input text inserted into the query string. QR code readers are subject to data injection into their structured objects when they attempt to interpret the data of a QR code.
- A malicious party can create a QR code that injects arbitrary strings into a user’s data structures potentially causing harm to the user.
- Criminals can simply prepare malicious QR codes and affix them over legitimate codes which may result in victims inadvertently making payments to a criminal rather a legitimate service provider.
- QRLJacking or Quick Response Code Login Jacking is a simple social engineering attack vector capable of session hijacking affecting all applications that rely on “Login with QR code” feature as a secure way to login to accounts.
- QRLJacking attack gives attackers the ability to apply a full account hijacking scenario on the vulnerable Login with QR Code feature resulting in accounts stealing and reputation affection.
Source: DSCI
QR codes are capable of storing high quality data and its significance can be found in IoT applications as well. As more devices get connected, the more prone they are to attacks and QR codes can be one such blind spot for attacks if it is left untouched.
Going Forward
In a study done by Data Security Council Of India along with Paypal, the following tips were listed for the customers:
- Install a mobile security application with antivirus, antispyware and web filtering abilities to protect your mobile devices.
- If the QR code looks like it was added on to marketing materials, do not scan it.
- If the QR code leads you to a website that request for your personal information, do not disclose anything until you have verified that the request is legitimate.
- Do not scan QR codes in the form of stickers placed randomly in public places as it might be from scammers testing out his/her malicious QR code.
The concern of security of payment modes is more significant to countries like India, which has seen a sporadic rise in initiatives such as Bharat QR and UPI QR interoperable. The pursuit of large scale digitisation also exposes the systems to attacks such as discussed in the previous sections of the article. So far India hasn’t witnessed any significant malpractice using QR codes.
However, as India aims at reaching new heights in its digital payments journey, consumer trust and safety becomes critical and should be considered as a high priority.