In the past, we have seen SIM jacking attacks, where a hacker can impersonate a targeted victim to steal the cell phone number, which then can be used to access the victim’s unprotected assets. But, now cybersecurity researchers at AdaptiveMobile Security have identified a critical vulnerability in SIM cards that could allow remote attackers to compromise targeted mobile phones and spy on victims without their knowledge just by sending an SMS.
The vulnerability has been named ‘Simjacker’. The difference between SIM jacking and Simjacker vulnerability is that the former is a process that involves the impersonation of individuals using their SIM card information. AdaptiveMobile Security says this vulnerability has been exploited for at least the last 2 years by a highly sophisticated threat actor in multiple countries, primarily for the purposes of surveillance.
How Is The Attack Carried Out?
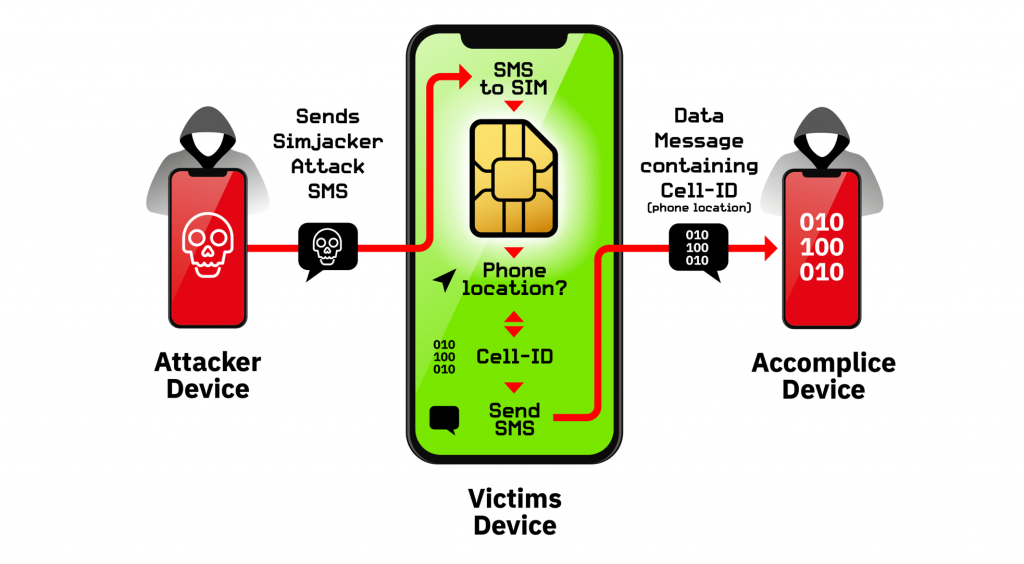
The Simjacker attack involves an SMS containing a particular kind of malicious code being sent to a mobile phone, which then instructs the universal integrated circuit card (UICC) or SIM Card inside the phone to be able to control the mobile phone to retrieve and execute sensitive commands.
The attack starts when a Simjacker Attack Message is pushed to a targeted handset from another remote device which contains a series of SIM Toolkit (STK) instructions specifically designed to be passed on to the SIM Card within the device. In order for these instructions to work, the attack exploits a kind of software, called the S@T Browser which is found on the SIM card. Once the Simjacker Attack Message is received by the SIM card, it uses the S@T Browser library as an execution environment on the SIM card, where it can trigger logic on the handset.
For the main attack, the Simjacker code running on the SIM card requests location and specific device information (the IMEI) from the handset. Once this information is retrieved, the Simjacker code running on the SIM card then collects it and sends the combined information to a remote phone controlled by the attacker, again by triggering logic on the handset. During the attack, the user is completely unaware that they received the SMS with the Simjacker Attack message, that information was retrieved, and that it was sent outwards as there is no indication in any SMS inbox or outbox.
By using the same technique, and by modifying the SMS the attackers can instruct the SIM card to execute an array of other types of attacks. Researchers at AdaptiveMobile Security were able to make targeted handsets open up web browsers, ring other phones, send text messages and so on by using the commands in their own tests. Researchers found that attackers can perform malicious activities like opening a browser and redirect to malicious webpages to install malware on the phone.
What May Be The Impact?
In theory, all makes and models of mobile phones are open to attack as the vulnerability is linked to a technology embedded on SIM cards. The Simjacker vulnerability could extend to over 1 billion mobile phone users globally, potentially impacting countries in the Americas, West Africa, Europe, Middle East and indeed any region of the world where this SIM card technology is in use. Many of its attacks seems to work independent of handset types, as the vulnerability is dependent on the software on the SIM card and not the device.
Cathal McDaid, Chief Technology Officer of AdaptiveMobile Security explained, “Simjacker represents a clear danger to the mobile operators and subscribers. This is potentially the most sophisticated attack ever seen over core mobile networks. It’s a major wake-up call that shows hostile actors are investing heavily in increasingly complex and creative ways to undermine network security. This compromises the security and trust of customers, mobile operators and impacts the national security of entire countries.”
Overview
Simjacker and its associated exploits is a huge jump in complexity and sophistication compared to attacks previously seen over mobile core networks. Adaptive Mobile Security recommends that immediate threat is for mobile operators to analyse and block suspicious messages that contain S@T Browser commands.
According to Adaptive Mobile Security analysts, mobile Operators can also change the security settings of SIMs or even uninstall and stop using the S@T Browser technology completely, but this may be slower and considerably more difficult to do. Simjacker also means that mobile operators will need to constantly investigate suspicious and malicious activity to discover hidden attacks. Operators will also need to increase their own abilities and investment in detecting and blocking these attacks as the attackers have expanded their abilities beyond simply exploiting unsecured networks, to now cover a very complex mix of protocols, execution environments and technologies.



















































































